The Department of Defense (DoD)
A Stronger Cyber Defense
The Department of Defense (DoD) must protect mission critical systems, sensitive data, and national security infrastructure from sophisticated cyber threats posed by state-sponsored actors, criminal organizations, and rogue entities. Situational awareness of everything is vital to ensure adversaries don’t know more about us than we do ourselves. But awareness alone is not enough. All assets are susceptible to vulnerabilities and risk; and it is essential to understand and prioritize them based on threat, risk, operational impact, and criticality. With risk presenting at varying levels, clear insight to make informed decisions and take appropriate action where it matters most is key to protect the success of your operation.
See, Protect, and Manage Your Entire Cyber Terrain
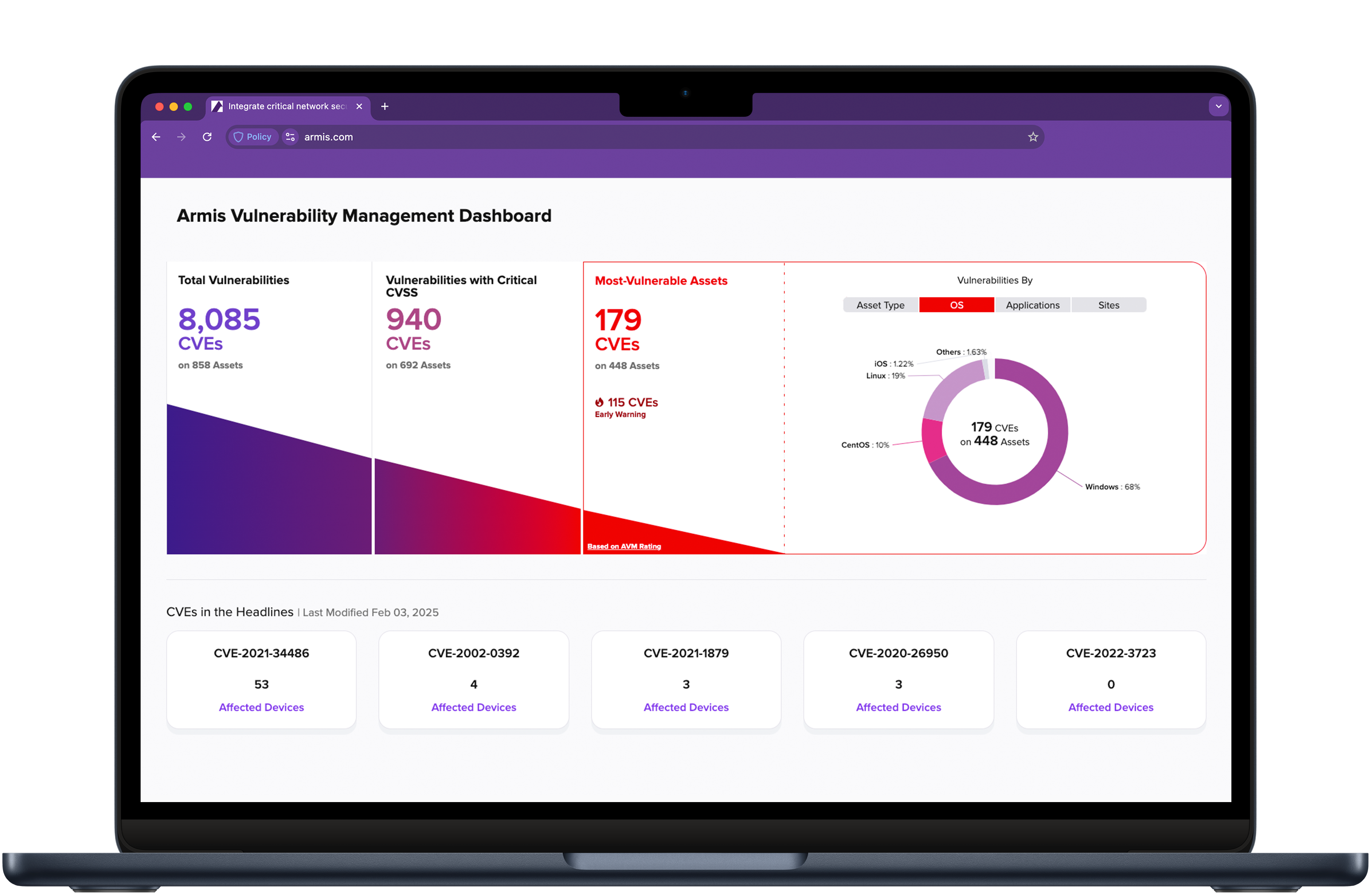
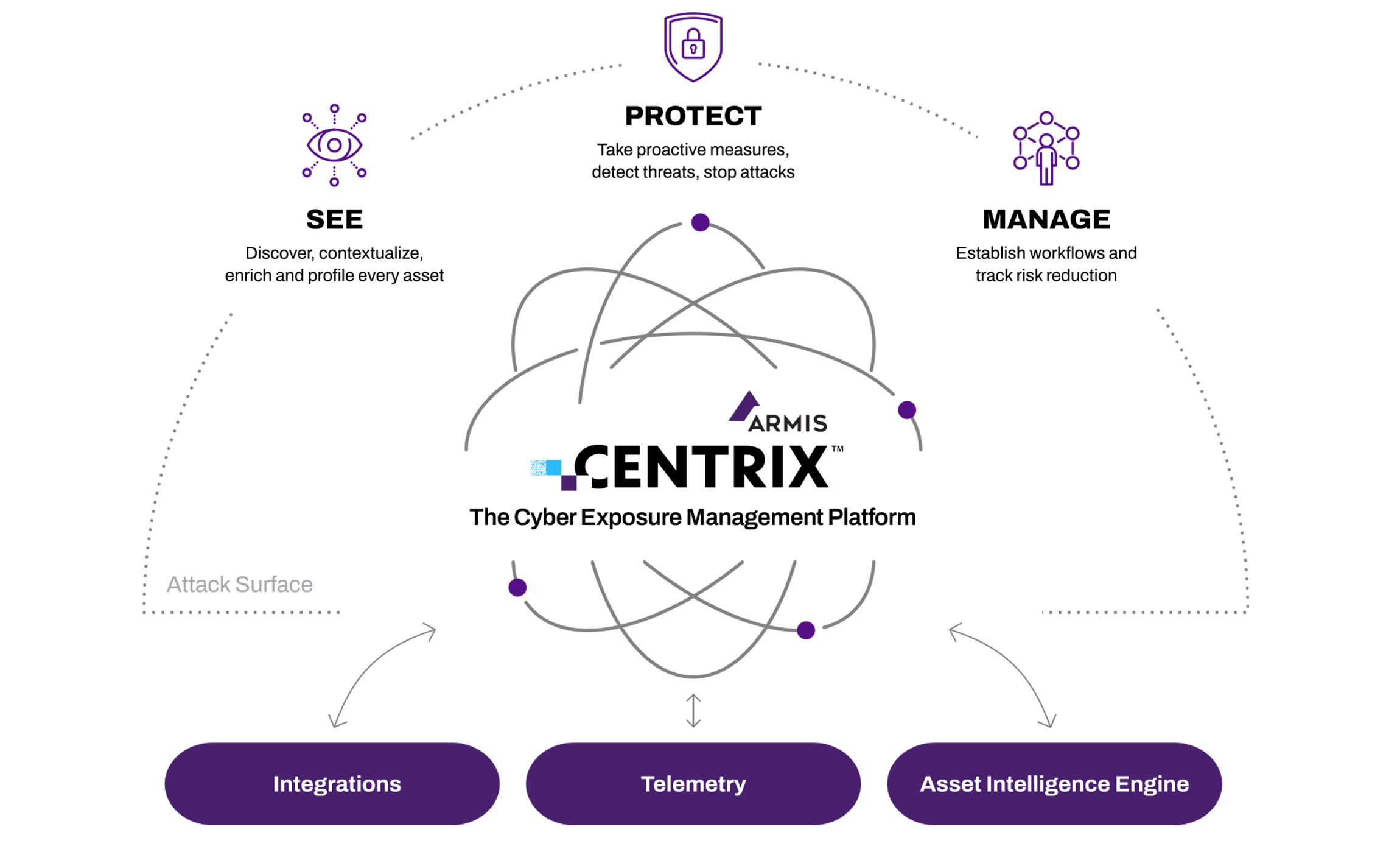
Armis Centrix™ enables the DoD to build a comprehensive cybersecurity program focused on: asset management and security, vulnerability & security finding, prioritization and remediation, OT/IoT security, medical device security, and early warning threat detection. It gives those defending our country peace of mind, knowing that all assets are protected in real time.
Addressing the Unique Challenges of the Department of Defense
The Push for Zero Trust
Zero Trust assumes, by default, that no person or device from inside or outside the network should be trusted. It relies on continuous monitoring of user and device behavior for granting or denying access to the network.
To close the visibility gap and secure the mission, the DoD needs a single, authoritative source of truth for all organizational assets. To realize the full promise of Zero Trust, it needs specialized capabilities for seeing and non-disruptively monitoring every asset.
Cybersecurity Maturity Model Certification (CMMC) Framework
Defense Industrial Base (DIB) contractors must secure sensitive information to comply with CMMC.
Spanning 110 controls from NIST SP 800-171 and, in some cases, NIST SP 800-172, the framework’s three compliance levels require advanced cyber exposure management and security practices. Contractors must self-assert or pass audits every three years to remain eligible for DoD contracts.
Limited Funding and Internal Resources
The DoD faces significant challenges in addressing cybersecurity threats due to limited funding and constrained internal resources. These limitations may hinder the ability to implement advanced security measures, maintain robust infrastructures, and effectively counter evolving cyberattacks.
Without adequate support, the DoD’s critical systems remain vulnerable to potential breaches and adversarial threats.
Enabling the Department of Defense’s Mission with Armis Centrix™

Early Warning
The foundation on which modern cyber programs build and optimize.
Asset Management and Security
Discover and classify every device in any environment.

Asset Intelligence
Gain the intelligence required from the Armis Asset Intelligence Engine which monitors and profiles billions of assets world-wide to identify cyber risk patterns.
Dynamic Risk Assessment
Individual risk assessments for each device based on real time intelligence and dynamic operating environments.
Vulnerability Management
Identify risk, deduplicate, contextualize, prioritize and assign in order to take the right action at the right time.

Zero Trust Strategy
Improve and streamline governance, security frameworks and compliance-related processes.